1. File Upload Vulns - Only allow safe files to be updated.
1. File Upload Vulns - Only allow safe files to be updated.
2. Code Execution Vulns:
Don‘t use dangerous functions.
Filter use input before execution.
3. File inclusion:
Disable allow_url_fopen & allow_url_include.
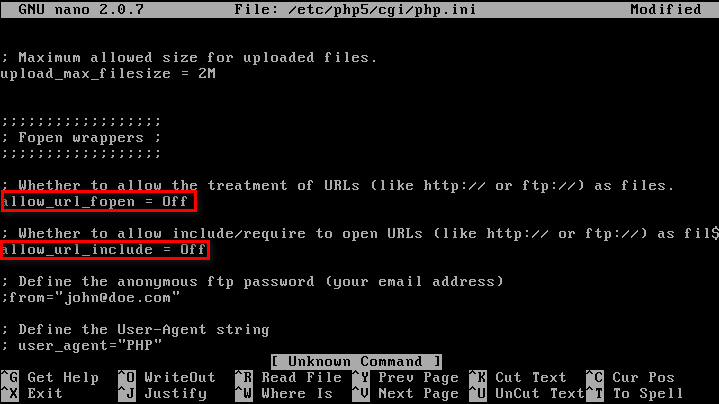
Use static file inclusion.
Suggest using Hard Code Style, not using any variables, which is much more secure.
index.php?page=news.php
index.php
code:
include($_GET(‘page‘));
index.php
code:
include(‘page.php‘);
Ethical Hacking - Web Penetration Testing(7)
,温馨提示: 本文由Jm博客推荐,转载请保留链接: https://www.jmwww.net/file/web/30337.html
- 上一篇:i年龄 web(2)
- 下一篇:为了使用此扩展我们还需要单独安装扩展


![[转]Node.js中package.json中^和~的区别 [转]Node.js中package.json中^和~的区别](/uploads/allimg/200519/054J34453_lit.png)